GLOBAL IT SALARY SURVEY
November 11, 2020
Several months ago, before the COVID-19 virus hit, I was talking to a young man interested in the STEM (Science, Technology, Engineering, Mathematics) professions. He was a graduating high school senior from Nashville and wondered what might be the future of technology as a profession. He asked me about IT and what I thought that course of work might provide in the way of a challenge, salary, stability, etc. In other words, all of those qualities we look for in a job. At that time, I did not have the information you are about to see regarding salary. My advice to him was go for the challenge and the money will follow. As it turns out, the bucks are there also. I’m going to make this a two-part post because the 2020 IT Skills and Salary Survey is very detailed. The first part involves salary. The second part discusses job satisfaction, certifications, and rate of advancement. Let’s now take a look.
The 2020 IT Skills and Salary Survey was conducted online from September 2019 through November 2019 using the Qualtrics XM Platform. Global Knowledge and technology companies distributed survey invitations to millions of professionals around the world, primarily in their databases. The survey was made available in web articles, online newsletters and social media. The survey yielded 9,505 completed responses. The survey was tabulated using the Qualtrics XM Platform.
An individual’s salary is determined by a combination of factors, including education, responsibility level, job role, certification, tenure, industry, company size and location. In the 2020 IT Skills and Salary Survey, the respondents were about these factors. Respondents came from all over the globe, consequently the results reflect their answers. Participants were required to convert their salaries into U.S. dollars while taking the survey to enable relevant comparisons.
BASE SALARY:
The average annual salary for global IT professionals is $85,115.

RAISES AND BONUSES: Nearly sixty percent (60%) of IT professionals received a raise in the past year. Raise percentages were consistent across all regions—four to six percent. The only outlier is decision-makers in Latin America whose salaries, on average, dropped two percent year over year. Thirty-seven percent (37%) of IT professionals who received a raise attribute it to job performance, while nearly thirty percent (30%) received a pay bump as part of a standard company increase. Fifteen percent (15%) saw their salary increase as part of a promotion. The reason for a raise impacts the amount of the raise. Twelve percent (12%) of individuals who received a raise attribute it to new skills—those same respondents earned nearly $12,000 more this year. IT professionals who obtained a new certification saw their salary increase nearly $13,000. Both of these numbers are strong indications that training pays off. Certifications are very important in the IT industry and form the basis for promotions.

Factors for increases salary are fairly standard and as you would expect with performance being the very first.

RECEIVED A BONUS:
Worldwide, sixty-six percent (66%) of eligible decision-makers and fifty-five percent (55%) of staff earned a bonus this year—both are up noticeably from 2019. In North America, seventy percent (70%) of decision-makers and fifty-seven percent (57%) of staff received bonuses. EMEA had the lowest numbers in this category, as only half of the eligible staff received a bonus.

SALARY BY RESPONSIBILITY LEVEL:
Even though the more senior IT personnel received the largest salaries, take a look at non-management “average” salary for North America. A whopping $105,736. That number goes down for other regions of the globe but still a big number.

CAREER EXPERIENCE:
Unsurprisingly, more tenured IT professionals have the highest salaries. Those with twenty-six (26) or more years of experience earn $120,098 a year—that’s more than double the average salary for first-year IT professionals. In North America, IT professionals cross the $100,000 threshold in years eleven to fifteen (11 to 15). The most tenured earn almost $140,000 a year. Among our respondents, the highest percentage has between six and fifteen (15) years of experience. Only one percent are in their first year, while thirteen percent (13%) have worked in tech for over a quarter of a century.

JOB FUNCTION:

SALARIES BY INDUSTRY:

U.S. SALARIES BY STATE:
IT professionals in the U.S. have an average annual salary of $120,491. U.S. decision-makers earn $138,200 a year. While tenure, job function and industry affect pay, geography is also a major salary influencer. The cost of living in the Mid-Atlantic or New England, for example, is higher than the Midwest. Washington, D.C. has the highest IT salaries in the country at $151,896—a nineteen percent (19%) increase from 2019. New Jersey, California, Maryland and New York round out the top five U.S. salaries by state. California had the highest U.S. salaries in 2019. South Dakota has the lowest average salary ($61,867) this year.

CANADIAN SALARIES:
The average annual salary in Canada is $77,580. IT professionals in British Columbia have the highest average salaries in the country at $85,801. The other top-paying Canadian provinces by salary are Quebec ($81,573), Ontario ($78,887), Alberta ($78,040) and Saskatchewan ($70,811). Provinces with fewer than 10 respondents were omitted from the list.

EUROPEAN SALARIES:
For the second straight year, Switzerland dominates European salaries with an annual average of $133,344. The average annual IT salary in Europe is $71,796. Germany has the second-highest salary at $88,195. Rounding out the top five is Ireland ($87,154), Belgium ($85,899) and the United Kingdom ($82,792). European countries with fewer than 30 respondents were omitted from the list.

CONCLUSIONS:
The next post will be tomorrow and will be Certifications and Job Satisfaction.
INFLUENCERS
June 6, 2020
Some of the most remarkably written articles are found in the publication “Building Design + Construction”. This monthly magazine highlights architecture, engineering and construction (AEC) describes building projects and designs around the world. Many projects underway are re-construction and/or refurbishment of existing structures; i.e. schools, churches, office buildings, etc. The point I’m trying to make, the writing is superb, innovative and certainly relevant. The April edition featured INFLUENCERS.
If you investigate websites, you will find an ever-increasing number of articles related to Influencer Marketing. Influencer marketing is becoming, or I should say, is a significant factor in a person choosing one product over another. One of our granddaughters is an influencer and her job is fascinating. Let’s look.
DEFINITION:
- the power to affect the purchasing decisions of others because of his or her authority, knowledge, position, or relationship with his or her audience.
- a following in a distinct niche, with whom he or she actively engages. The size of the following depends on the size of his/her topic of the niche.
CLASSIFICATIONS:
There are various classifications depending upon circumstances. Those are given below.
Mega-Influencers— Mega influencers are the people with a vast number of followers on their social networks. Facebook, Instagram, Twitter, Snapchat, Utube, etc. are social instruments upon which influencers ply their trade. Although there are no fixed rules on the boundaries between the different types of followers, a common view is that mega-influencers have more than 1 million followers on at least one social platform. President Donald Trump, Kim Kardashian, Hillary Clinton and of course several others may be classified as Mega-influencers.
Macro-Influencers—Macro-influencers are one step down from the mega-influencers, and maybe more accessible as influencer marketers. You would consider people with followers in the range between 40,000 and one million followers on a social network to be macro-influencers.
This group tends to consist of two types of people. They are either B-grade celebrities, who haven’t yet made it to the big time. Or they are successful online experts, who have built up more significant followings than the typical micro-influencers. The latter type of macro-influencer is likely to be more useful for firms engaging in influencer marketing.
Micro-Influencers— Micro-influencers are ordinary everyday people who have become known for their knowledge about some specialist niche. As such, they have usually gained a sizable social media following amongst devotees of that niche. Of course, it is not just the number of followers that indicates a level of influence; it is the relationship and interaction that a micro-influencer has with his or her followers.
Nano-Influencers—The newest influencer-type to gain recognition is the nano-influencer. These people only have a small number of followers, but they tend to be experts in an obscure or highly specialized field. You can think of nano-influencers as being the proverbial big fish in a small pond. In many cases, they have fewer than one thousand (1,000) followers – but they will be keen and interested followers, willing to engage with the nano-influencer, and listen to his/her opinions.
If we look further, we can “drill down” to the various internet providers hosting the influencer packages.
Bloggers— Bloggers and influencers in social media have the most authentic and active relationships with their fans. Brands are now recognizing and encouraging this. Blogging has been connected to influencer marketing for some time now. There are many highly influential blogs on the internet. If a popular blogger positively mentions your product in a post, it can lead to the blogger’s supporters wanting to try out the specific product.
YouTubers—Rather than each video maker having their own site, most create a channel on YouTube. Brands often align with popular YouTube content creators.
Podcasts— Podcasting is a relatively recent form of online content that is growing in great popularity. It has made quite a few household names now, possibly best epitomized by John Lee Dumas of Entrepreneurs on Fire. If you have not yet had the opportunity to enjoy podcasts, Digital Trends has put together a comprehensive list of the best podcasts of 2019. Our youngest son has a podcast called CalmCash. He does a great job and is remarkably creative.
Social Posts Only— The vast majority of influencers now make their name on social media. While you will find influencers on all leading social channels, the standout network in recent years has been Instagram, where many influencers craft their posts around various stunning images.
Now, if we go back to “Building Design + Construction”, they interviewed five influencers that apply their skills to the AEC profession. I will give you, through their comments, the thrust of their efforts:
CHRISTINE WILLIAMSON— “My goal is to help teach architects about building science and construction. I want to show how the “AEC” parts fit together.”
BOB BORSON—He is the cohost of the Life of an Architect podcast which gets about two hundred and sixty (260) downloads per day. He would be a nano-influencer. “Influencer” is a ridiculous word. If you have to tell people you’re an influencer, you’re not”. His words only.
AMY BAKER—Launched her Instagram account in 2018 and is the host for SpecFunFacts. She discusses specifications and contracts and has around one thousand (1,000) followers.
CATHERINE MENG– Ms. Meng is the host of the Design Voice podcast.
MATT RISENGER—Mr. Risenger hosts “Buildshownetwork”. He first published Matt Risinger’s Green Building blog in 2006. This was the manner in which he publicized his new homebuilding company in Austin, Texas. To date, he has seven hundred (700) plus videos on YouTube. Right now, he has six hundred thousand (600,000) subscribers.
CONCLUSIONS: From the above descriptions and the five individual influencers detailed in the AEC magazine, you can get some idea as to how influencers ply their trade and support design and building endeavors. Hope you enjoyed this one.
TELECOMMUTING
March 13, 2019
Our two oldest granddaughters have new jobs. Both, believe it or not, telecommute. That’s right, they do NOT drive to work. They work from home—every day of the week and sometimes on Saturday. Both ladies work for companies not remotely close to their homes in Atlanta. The headquarters for these companies are hundreds of miles away and in other states.
Even the word is fairly new! A few years ago, there was no such “animal” as telecommuting and today it’s considered by progressive companies as “kosher”. Companies such as AT&T, Blue Cross-Blue Shield, Southwest Airlines, The Home Shopping Network, Amazon and even Home Depot allow selected employees to “mail it in”. The interesting thing; efficiency and productivity are not lessened and, in most cases, improve. Let’s look at several very interesting facts regarding this trend in conducting business. This information comes from a website called “Flexjobs.com”.
- Three point three (3.3) million full-time professionals, excluding volunteers and the self-employed, consider their home as their primary workplace.
- Telecommuting saves between six hundred ($600) and one thousand ($1,000) on annual dry-cleaning expenses, more than eight hundred ($800) on coffee and lunch expenses, enjoy a tax break of about seven hundred and fifty ($750), save five hundred and ninety ($590) on their professional wardrobe, save one thousand one hundred and twenty ($1,120) on gas, and avoid over three hundred ( $300 ) dollars in car maintenance costs.
- Telecommuters save two hundred and sixty (260) hours by not commuting on a daily basis.
- Work from home programs help businesses save about two thousand ($2,000) per year help businesses save two thousand ($2,000) per person per year and reduce turnover by fifty (50%) percent.
- Typical telecommuter are college graduates of about forty-nine (49) years old and work with a company with fewer than one hundred (100) employees.
- Seventy-three percent (73%) of remote workers are satisfied with the company they work for and feel that their managers are concerned about their well-being and morale.
- For every one real work-from-home job, there are sixty job scams.
- Most telecommuters (53 percent) work more than forty (40) hours per week.
- Telecommuters work harder to create a friendly, cooperative, and positive work environment for themselves and their teams.
- Work-from-home professionals (82 percent) were able to lower their stress levels by working remotely. Eighty (80) percent have improved morale, seventy (70) percent increase productivity, and sixty-nine (69) percent miss fewer days from work.
- Half of the U.S. workforce have jobs that are compatible with remote work.
- Remote workers enjoy more sleep, eat healthier, and get more physical exercise
- Telecommuters are fifty (50) percent less likely to quit their jobs.
- When looking at in-office workers and telecommuters, forty-five (45) percent of telecommuters love their job, while twenty-four (24) percent of in-office workers love their jobs.
- Four in ten (10) freelancers have completed projects completely from home.
OK, what are the individual and company benefits resulting from this activity. These might be as follows:
- Significant reduction in energy usage by company.
- Reduction in individual carbon footprint. (It has been estimated that 9,500 pounds of CO 2 per year per person could be avoided if the employee works from home. Most of this is avoidance of cranking up the “tin lezzy”.)
- Reduction in office expenses in the form of space, desk, chair, tables, lighting, telephone equipment, and computer connections, etc.
- Reduction in the number of sick days taken due to illnesses from communicable diseases.
- Fewer “in-office” distractions allowing for greater focus on work. These might include: 1.) Monday morning congregation at the water cooler to discuss the game on Saturday, 2.) Birthday parties, 3.) Mary Kay meetings, etc etc. You get the picture!
In the state where I live (Tennessee), the number of telecommuters has risen eighteen (18) percent relative to 2011. 489,000 adults across Tennessee work from home on a regular basis. Most of these employees do NOT work for themselves in family-owned businesses but for large companies that allow the activity. Also, many of these employees work for out-of-state concerns thus creating ideal situations for both worker and employer. At Blue Cross of Tennessee, one in six individuals go to work by staying at home. Working at home definitely does not always mean there is no personal communication with supervisors and peers. These meetings are factored into each work week, some required at least on a monthly basis.
Four point three (4.3) million employees (3.2% of the workforce) now work from home at least half the time. Regular work-at-home, among the non-self-employed population, has grown by 140% since 2005, nearly 10x faster than the rest of the workforce or the self-employed. Of course, this marvelous transition has only been made possible by internet connections and in most cases; the computer technology at home equals or surpasses that found at “work”. We all know this trend will continue as well it should.
I welcome your comments and love to know your “telecommuting” stories. Please send responses to: bobjengr@comcast.net.
DECISION PARALYSIS
January 5, 2019
The idea for this post came from “Plant Engineering Magazine”, December 2018.
OK, now what do I do? Have you ever heard yourself muttering those words? Well, I’ve been there—done that—got the “Tee shirt”. We all have at one time been placed or have placed ourselves in the decision-making process with a certain degree of paralysis. If you have P and L responsibilities, own a house, contemplate the purchase of any item that will impact your checkbook or finances, you’ve been there. Let’s take a look at eight (8) factors that may cause decision paralysis.
- RAPID CHANGE: The manner in which we conduct our daily lives has changed dramatically over the past few years. Digitalization is sweeping across the domestic and commercial world changing the way we do just about everything. The way we shop, bank, and travel can be accomplished on-line with delivery systems reacting accordingly. Everyone, including the
“ baby-boomers” need to get on-board with the changes. - COMPLEX PROCESSES: Old-school processes are inadequate for managing today’s very complex issues. Our three sons and all of our grandchildren have probably never purchased a stamp. Everything is accomplished on line including paying the bills. There will come a time when every acquisition will start online. One of the most fascinating web sites if U-tube.com. I have never been faced with a “fix-it” problem that is not described on U-tube. It is a valuable resource. Get ready for digitization now—its coming.
- DEMANDING CUSTOMERS: Today’s consumers have high expectations for attentive service, high value, and timely communication. It is no longer enough to be content with trusting the process will deliver value for the customer. My greatest complaint with COMCAST is customer service. The product itself is adequate but their customer service is one of the most pitiful on the planet.
- PHYSICAL THREATS: I do NOT mean burglars and home invasion. Aging infrastructure systems, including our power grid, air traffic control, bridges, railways, pose significant threats to reliable communication, transportation and safety in general. In-house and in-store equipment may not be sophisticated enough to handle growing demands brought on by our “digital world”. Upgrades to physical equipment and programs driving that equipment become more frequent as we try to make decisions and choices.
- TOO MANY CHOICES: While choices are really nice, too many options can present a real burden for the decision maker. We should and must prioritize the growing list of choices and choose the most viable options. This includes possible vendors and companies offering choices.
- CYBER THREATS: We MUST incorporate systems to protect digital infrastructure. If you read the literature, you find we are losing that battle. It’s almost to the point that every household needs an IT guy.
- DATA OVERLOAD: “Big data” is swamping us with information at an ever-growing rate due to an endless list of features and functionality relative to digital devices. As you well know, CDs and DVDs can now be purchased with terabyte capabilities. Necessity is the mother of invention and this need will only grow.
- TIGHT BUDGETS AND FINANCES: In most cases, making the proper and correct decision will require some cost. Once again, this can cause delays in trying to choose the best options with the maximum payback in time, money and effort.
There may be others factors depending upon the situation or the decision you must make on a personal basis. Let us now consider steps that just might ease the pain of decision-making.
- EARLY DETECTION OF A PROBLEM: There probably are early warning signs that a problem is coming necessitating a solution. It is a great help if you can stay attuned to warnings that present themselves. It gives you time to consider a possible solution.
- SCHEDULE AND CONSIDER YOUR “FIX” EARLY: If at all possible, solve the problem before it becomes a panic situation. Have a solution or solutions ready to incorporate by becoming pro-active.
- MONITOR THE FIX: Make sure you are solving the problem and not a manifestation of the problem. We call this “root-cause-analysis”.
- TRACK YOUR COSTS: Know what it costs to resolve the problem.
- MAINTAIN RECORDS AND CREATE A PAPER TRAIL: Some times the only way you know where you are is to look back to see where you have been!
HOW MUCH IS TOO MUCH?
December 15, 2018
How many “screen-time” hours do you spend each day? Any idea? Now, let’s face facts, an adult working a full-time job requiring daily hour-long screen time may be a necessity. We all know that but how about our children and grandchildren?
I’m old enough to remember when television was a laboratory novelty and telephones were “ringer-types” affixed to the cleanest wall in the house. No laptops, no desktops, no cell phones, no Gameboys, etc etc. You get the picture. That, as we all know, is a far cry from where we are today.
Today’s children have grown up with a vast array of electronic devices at their fingertips. They can’t imagine a world without smartphones, tablets, and the internet. If you do not believe this just ask them. One of my younger grandkids asked me what we did before the internet. ANSWER: we played outside, did our chores, called our friends and family members.
The advances in technology mean today’s parents are the first generation who have to figure out how to limit screen-time for children. This is a growing requirement for reasons we will discuss later. While digital devices can provide endless hours of entertainment and they can offer educational content, unlimited screen time can be harmful. The American Academy of Pediatrics recommends parents place a reasonable limit on entertainment media. Despite those recommendations, children between the ages of eight (8) and eighteen (18) average seven and one-half (7 ½) hours of entertainment media per day, according to a 2010 study by the Henry J. Kaiser Family Foundation. Can you imagine over seven (7) hours per day? When I read this it just blew my mind.
But it’s not just kids who are getting too much screen time. Many parents struggle to impose healthy limits on themselves too. The average adult spends over eleven (11) hours per day behind a screen, according to the Kaiser Family Foundation. I’m very sure that most of this is job related but most people do not work eleven hours behind their desk each day.
Let’s now look at what the experts say:
- Childrenunder age two (2) spend about forty-two (42) minutes, children ages two (2) to four (4) spend two (2) hours and forty (40) minutes, and kids ages five (5) to eight (8) spend nearly three (3) hours (2:58) with screen media daily. About thirty-five (35) percent of children’s screen time is spent with a mobile device, compared to four (4) percent in 2011. Oct 19, 2017
- Children aged eighteen (18) monthsto two (2) years can watch or use high-quality programs or apps if adults watch or play with them to help them understand what they’re seeing. children aged two to five (2-5) years should have no more than one hour a day of screen time with adults watching or playing with them.
- The American Academy of Pediatrics released new guidelines on how much screen timeis appropriate for children. … Excessive screen time can also lead to “Computer Vision Syndrome” which is a combination of headaches, eye strain, fatigue, blurry vision for distance, and excessive dry eyes. August 21, 2017
- Pediatricians: No More than two (2) HoursScreen Time Daily for Kids. Children should be limited to less than two hours of entertainment-based screen time per day, and shouldn’t have TVs or Internet access in their bedrooms, according to new guidelines from pediatricians. October 28, 2013
OK, why?
- Obesity: Too much time engaging in sedentary activity, such as watching TV and playing video games, can be a risk factor for becoming overweight.
- Sleep Problems: Although many parents use TV to wind down before bed, screen time before bed can backfire. The light emitted from screens interferes with the sleep cycle in the brain and can lead to insomnia.
- Behavioral Problems: Elementary school-age children who watch TV or use a computer more than two hours per day are more likely to have emotional, social, and attention problems. Excessive TV viewing has even been linked to increased bullying behavior.
- Educational problems: Elementary school-age children who have televisions in their bedrooms do worse on academic testing. This is an established fact—established. At this time in our history we need educated adults that can get the job done. We do not need dummies.
- Violence: Exposure to violent TV shows, movies, music, and video games can cause children to become desensitized to it. Eventually, they may use violence to solve problems and may imitate what they see on TV, according to the American Academy of Child and Adolescent Psychiatry.
When very small children get hooked on tablets and smartphones, says Dr. Aric Sigman, an associate fellow of the British Psychological Society and a Fellow of Britain’s Royal Society of Medicine, they can unintentionally cause permanent damage to their still-developing brains. Too much screen time too soon, he says, “is the very thing impeding the development of the abilities that parents are so eager to foster through the tablets. The ability to focus, to concentrate, to lend attention, to sense other people’s attitudes and communicate with them, to build a large vocabulary—all those abilities are harmed.”
Between birth and age three, for example, our brains develop quickly and are particularly sensitive to the environment around us. In medical circles, this is called the critical period, because the changes that happen in the brain during these first tender years become the permanent foundation upon which all later brain function is built. In order for the brain’s neural networks to develop normally during the critical period, a child needs specific stimuli from the outside environment. These are rules that have evolved over centuries of human evolution, but—not surprisingly—these essential stimuli are not found on today’s tablet screens. When a young child spends too much time in front of a screen and not enough getting required stimuli from the real world, her development becomes stunted.
CONCLUSION: This digital age is wonderful if used properly and recognized as having hazards that may create lasting negative effects. Use wisely.
SOCIAL MEDIA
June 27, 2018
DEFINITION:
Social media is typically defined today as: – “Web sites and applications that enable users to create and share content or to participate in social networking” – OxfordDictionaries.
Now that we have cleared that up, let’s take a look at the very beginning of social media.
Six Degrees, according to several sources, was the first modern-day attempt of providing access to communication relative to the “marvelous world” of social media. (I have chosen to put marvelous world in quotes because I’m not too sure it’s that marvelous. There is an obvious downside.) Six Degrees was launched in 1997 and definitely was the first modern social network. It allowed users to create a profile and to become friends with other users. While the site is no longer functional, at one time it was actually quite popular and had approximately a million members at its peak.
Other sources indicate that social media has been around for the better part of forty (40) years with Usenet appearing in 1979. Usenet is the first recorded network that enabled users to post news to newsgroups. Although these Usenets and similar bulletin boards heralded the launch of the first, albeit very rudimentary, social networks, social media never really took off until almost thirty (30) years later, following the roll out of Facebook in 2006. Usenet was not identified as “social media” so the exact term was not used at that time.
If we take a very quick look at Internet and Social Media usage, we find the following:
As you can see from above, social media is incredibly popular and in use hourly if not minute-by-minute. It’s big in our society today across the world and where allowed.
If we look at the fifteen most popular sites we see the following:
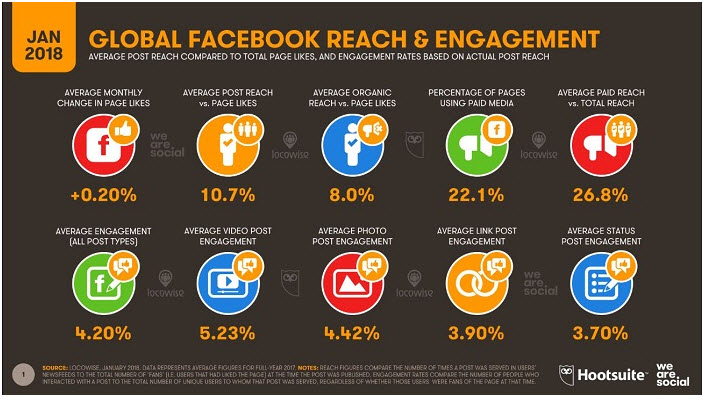
With out a doubt, the gorilla in the room is Facebook.
Facebook statistics
- Facebook adds 500,000 new users a day – that’s six new profiles a second – and just under a quarter (775) of adults in the US visit their account at least once a month
- The average (mean) number of Facebook friends is 155
- There are 60 million active small business pages (up from 40 million in 2015), 5 million of which pay for advertising
- There are thought to be 270 million fake Facebook profiles (there were only81 million in 2015)
- Facebook accounts for 1% of social logins made by consumers to sign into the apps and websites of publishers and brands.
It’s important we look at all social media sites so If we look at daily usage for the most popular web sites, we see the following:
BENEFITS:
- Ability to connect to other people all over the world. One of the most obvious pros of using social networks is the ability to instantly reach people from anywhere. Use Facebook to stay in touch with your old high school friends who’ve relocated all over the country, get on Google Hangouts with relatives who live halfway around the world, or meet brand new people on Twitter from cities or regions you’ve never even heard of before.
- Easy and instant communication. Now that we’re connected wherever we go, we don’t have to rely on our landlines, answering machines or snail mail to contact somebody. We can simply open up our laptops or pick up our smartphones and immediately start communicating with anyone on platforms like Twitter or one of the many social messaging apps
- Real-time news and information discovery. Gone are the days of waiting around for the six o’clock news to come on TV or for the delivery boy to bring the newspaper in the morning. If you want to know what’s going on in the world, all you need to do is jump on social media. An added bonus is that you can customize your news and information discovery experiences by choosing to follow exactly what you want.
- Great opportunities for business owners. Business owners and other types of professional organizations can connect with current customers, sell their products and expand their reach using social media. There are actually lots of entrepreneurs and businesses out there that thrive almost entirely on social networks and wouldn’t even be able to operate without it.
- General fun and enjoyment. You have to admit that social networking is just plain fun sometimes. A lot of people turn to it when they catch a break at work or just want to relax at home. Since people are naturally social creatures, it’s often quite satisfying to see comments and likes show up on our own posts, and it’s convenient to be able to see exactly what our friends are up to without having to ask them directly.
DISADVANTAGES:
- Information overwhelm. With so many people now on social media tweeting links and posting selfies and sharing YouTube videos, it sure can get pretty noisy. Becoming overwhelmed by too many Facebook friends to keep up with or too many Instagram photos to browse through isn’t all that uncommon. Over time, we tend to rack up a lot of friends and followers, and that can lead to lots of bloated news feeds with too much content we’re not all that interested in.
- Privacy issues. With so much sharing going on, issues over privacy will always be a big concern. Whether it’s a question of social sites owning your content after it’s posted, becoming a target after sharing your geographical location online, or even getting in trouble at work after tweeting something inappropriate – sharing too much with the public can open up all sorts of problems that sometimes can’t ever be undone.
- Social peer pressure and cyber bullying. For people struggling to fit in with their peers – especially teens and young adults – the pressure to do certain things or act a certain way can be even worse on social media than it is at school or any other offline setting. In some extreme cases, the overwhelming pressure to fit in with everyone posting on social media or becoming the target of a cyber-bullying attack can lead to serious stress, anxiety and even depression.
- Online interaction substitution for offline interaction. Since people are now connected all the time and you can pull up a friend’s social profile with a click of your mouse or a tap of your smartphone, it’s a lot easier to use online interaction as a substitute for face-to-face interaction. Some people argue that social media actually promotes antisocial human behavior.
- Distraction and procrastination. How often do you see someone look at their phone? People get distracted by all the social apps and news and messages they receive, leading to all sorts of problems like distracted driving or the lack of gaining someone’s full attention during a conversation. Browsing social media can also feed procrastination habits and become something people turn to in order to avoid certain tasks or responsibilities.
- Sedentary lifestyle habits and sleep disruption. Lastly, since social networking is all done on some sort of computer or mobile device, it can sometimes promote too much sitting down in one spot for too long. Likewise, staring into the artificial light from a computer or phone screen at night can negatively affect your ability to get a proper night’s sleep. (Here’s how you can reduce that blue light, by the way.)
Social media is NOT going away any time soon. Those who choose to use it will continue using it although there are definite privacy issues. The top five (5) issues discussed by users are as follows:
- Account hacking and impersonation.
- Stalking and harassment
- Being compelled to turn over passwords
- The very fine line between effective marketing and privacy intrusion
- The privacy downside with location-based services
I think these issues are very important and certainly must be considered with using ANY social media platform. Remember—someone is ALWAYS watching.
CAN YOU RETIRE
May 29, 2018
At some time in our working future we all hope to retire, but one burning question lingers—can you retire on what you have or will save at that point? We are told that:
At some point in your life, you’ll be using this money to support your lifestyle. By the time you reach sixty (60), you should have six times your salary saved – that’s $360,000 if you make $60,000 per year. Unfortunately, the average sixty-something has an estimated median of $172,000 in the bank. That is an estimate as of December 8, 2016. Nearly half of American families have no retirement account savings at all. This really blows my mind but this fact is what we are told by the Economic Policy Institute (EPI) in a new report entitled, “The State of American Retirement”. Please take a look at the graphic below and you can see age groups vs retirement account savings.
Whereas the average savings of a family with members in the 32-to-37 age range is $31,644, the median savings is a bleak $480. At the other end, the average savings of families 56 to 61 — those nearest to retirement — is $163,557. The median is $17,000.
I think there are very specific reasons for the lack of savings, especially for younger citizens of our country. Student loans, cost of living, pay scales, credit card debt, living above ones means, etc. all contribute to the inability to save or at least save enough for retirement.
The web site called MoneyWise.com has a very interesting solution to this problem or possible solution. If you go to this web site and look up the following post: “Places You can Retire to for Less Than $200K” you will see a list of twenty (20) countries that can supply most if not all of your needs if your retirement is less than $200 K. Let’s take a look at the list in order of favorability.
Thailand
Costa Rica
Nicaragua
Malaysia
Mexico
Malta
Ecuador
Spain
Portugal
Panama
Australia
Austria
Czech Republic
Slovenia
Chile
Uruguay
Vietnam
Guam
Indonesia
South Africa
MoneyWise.com completed a study comparing housing availability, cost of living, health care, crime, government and several other indicators to compile this list. It is a very interesting study and I encourage you to take a look even if you are not considering being an expatriate. You just might change your mind.
There are two other web sites I definitely recommend you check out as follows: 1.) The CIA Fact Book and 2.) Lonely Planet. From these two you will find very valuable information relative to any country you wish to research. Look before you leap might just be in order here. Another option might be spending time and not completely relocating. Two, three, six or even nine months during one year might get you beyond worry relative to being able to afford retirement on what you have saved. The most important thing is to DO THE RESEARCH. Make a list, then a short list of the countries that represent the leading candidates. THEN MAKE A VISIT. Wade—don’t jump. Several other considerations I would list are as follows:
- Make sure you consider your family, friends and support group before you make the move. Will they be willing and able to visit on a regular basis if needed?
- A huge factor for me would be availability of good if not excellent medical facilities.
- Cost of transportation.
- Language considerations. If English is an issue, how difficult would learning their language be?
- Power supplied. (I know this is off the wall.) Does the country provide 120-volt AC, 60 cycles per second or do they provide another voltage and frequency? In other words, will your electronics work? Will you have to buy new equipment or can a converter do the job?
- How difficult and costly is communication “back home”? This includes Internet services.
- Viability of local banking institutions
- Stability of government
- Weather factors
This is where good research is a MUST.
OKAY, TELL ME THE DIFFERENCE
March 21, 2018
Portions of this post are taken from the January 2018 article written by John Lewis of “Vision Systems”.
I feel there is considerable confusion between Artificial Intelligence (AI), Machine Learning and Deep Learning. Seemingly, we use these terms and phrases interchangeably and they certainly have different meanings. Natural Learning is the intelligence displayed by humans and certain animals. Why don’t we do the numbers:
AI:
Artificial Intelligence refers to machines mimicking human cognitive functions such as problem solving or learning. When a machine understands human speech or can compete with humans in a game of chess, AI applies. There are several surprising opinions about AI as follows:
- Sixty-one percent (61%) of people see artificial intelligence making the world a better place
- Fifty-seven percent (57%) would prefer an AI doctor perform an eye exam
- Fifty-five percent (55%) would trust an autonomous car. (I’m really not there as yet.)
The term artificial intelligence was coined in 1956, but AI has become more popular today thanks to increased data volumes, advanced algorithms, and improvements in computing power and storage.
Early AI research in the 1950s explored topics like problem solving and symbolic methods. In the 1960s, the US Department of Defense took interest in this type of work and began training computers to mimic basic human reasoning. For example, the Defense Advanced Research Projects Agency (DARPA) completed street mapping projects in the 1970s. And DARPA produced intelligent personal assistants in 2003, long before Siri, Alexa or Cortana were household names. This early work paved the way for the automation and formal reasoning that we see in computers today, including decision support systems and smart search systems that can be designed to complement and augment human abilities.
While Hollywood movies and science fiction novels depict AI as human-like robots that take over the world, the current evolution of AI technologies isn’t that scary – or quite that smart. Instead, AI has evolved to provide many specific benefits in every industry.
MACHINE LEARNING:
Machine Learning is the current state-of-the-art application of AI and largely responsible for its recent rapid growth. Based upon the idea of giving machines access to data so that they can learn for themselves, machine learning has been enabled by the internet, and the associated rise in digital information being generated, stored and made available for analysis.
Machine learning is the science of getting computers to act without being explicitly programmed. In the past decade, machine learning has given us self-driving cars, practical speech recognition, effective web search, and a vastly improved understanding of the human genome. Machine learning is so pervasive today that you probably use it dozens of times a day without knowing it. Many researchers also think it is the best way to make progress towards human-level understanding. Machine learning is an application of artificial intelligence (AI) that provides systems the ability to automatically learn and improve from experience without being explicitly programmed. Machine learning focuses on the development of computer programs that can access data and use it learn for themselves.
DEEP LEARNING:
Deep Learning concentrates on a subset of machine-learning techniques, with the term “deep” generally referring to the number of hidden layers in the deep neural network. While conventional neural network may contain a few hidden layers, a deep network may have tens or hundreds of layers. In deep learning, a computer model learns to perform classification tasks directly from text, sound or image data. In the case of images, deep learning requires substantial computing power and involves feeding large amounts of labeled data through a multi-layer neural network architecture to create a model that can classify the objects contained within the image.
CONCLUSIONS:
Brave new world we are living in. Someone said that AI is definitely the future of computing power and eventually robotic systems that could possibly replace humans. I just hope the programmers adhere to Dr. Isaac Asimov’s three laws:
- The First Law of Robotics: A robot may not injure a human being or, through inaction, allow a human being to come to harm.
- The Second Law of Robotics: A robot must obey the orders given to it by human beings, except where such orders would conflict with the First Law.
- The Third Law of Robotics: A robot must protect its own existence as long as such protection does not conflict with the First or Second Laws.
With those words, science-fiction author Isaac Asimov changed how the world saw robots. Where they had largely been Frankenstein-esque, metal monsters in the pulp magazines, Asimov saw the potential for robotics as more domestic: as a labor-saving device; the ultimate worker. In doing so, he continued a literary tradition of speculative tales: What happens when humanity remakes itself in its image?
As always, I welcome your comments.
OKAY—LOOK WHO’S LISTENING
February 7, 2018
The convergence of “smart” microphones, new digital signal processing technology, voice recognition and natural language processing has opened the door for voice interfaces. Let’s first define a “smart device”.
A smart device is an electronic device, generally connected to other devices or networks via different wireless protocols such as Bluetooth, NFC, Wi-Fi, 3G, etc., that can operate to some extent interactively and autonomously.
I am told by my youngest granddaughter that all the cool kids now have in-home, voice-activated devices like Amazon Echo or Google Home. These devices can play your favorite music, answer questions, read books, control home automation, and all those other things people thought the future was about in the 1960s. For the most part, the speech recognition of the devices works well; although you may find yourself with an extra dollhouse or two occasionally. (I do wonder if they speak “southern” but that’s another question for another day.)
A smart speaker is, essentially, a speaker with added internet connectivity and “smart assistant” voice-control functionality. The smart assistant is typically Amazon Alexa or Google Assistant, both of which are independently managed by their parent companies and have been opened up for other third-parties to implement into their hardware. The idea is that the more people who bring these into their homes, the more Amazon and Google have a “space” in every abode where they’re always accessible.
Let me first state that my family does not, as yet, have a smart device but we may be inching in that direction. If we look at numbers, we see the following projections:
- 175 million smart devices will be installed in a majority of U.S. households by 2022 with at least seventy (70) million households having at least one smart speaker in their home. (Digital Voice Assistants Platforms, Revenues & Opportunities, 2017-2022. Juniper Research, November 2017.)
- Amazon sold over eleven (11) million Alexa voice-controlled Amazon Echo devices in 2016. That number was expected to double for 2017. (Smart Home Devices Forecast, 2017 to 2022(US) Forester Research, October 2017.
- Amazon Echo accounted for 70.6% of all voice-enabled speaker users in the United States in 2017, followed by Google Home at 23.8%. (eMarketer, April 2017)
- In 2018, 38.5 million millennials are expected to use voice-enabled digital assistants—such as Amazon Alexa, Apple Siri, Google Now and Microsoft Cortana—at least once per month. (eMarketer, April 2017.)
- The growing smart speaker market is expected to hit 56.3 million shipments, globally in 2018. (Canalys Research, January 2018)
- The United States will remain the most important market for smart speakers in 2018, with shipments expected to reach 38.4 million units. China is a distant second at 4.4 million units. (Canalys Research, April 2018.)
With that being the case, let’s now look at what smart speakers are now commercialized and available either as online purchases or retail markets:
- Amazon Echo Spot–$114.99
- Sonos One–$199.00
- Google Home–$129.00
- Amazon Echo Show–$179.99
- Google Home Max–$399.00
- Google Home Mini–$49.00
- Fabriq Choros–$69.99
- Amazon Echo (Second Generation) –$$84.99
- Harman Kardon Evoke–$199.00
- Amazon Echo Plus–$149.00
CONCLUSIONS: If you are interested in purchasing one from the list above, I would definitely recommend you do your homework. Investigate the services provided by a smart speaker to make sure you are getting what you desire. Be aware that there will certainly be additional items enter the marketplace as time goes by. GOOD LUCK.








MEMORY LOSS AND STATISTICS
April 3, 2022
A good friend of mine sent me this very very interesting group of statistics. We both are considerable older that sixty-five years and constantly try to keep our spirits up relative to getting older. I thought these facts would interest you also. Here we go:
Considering a class size of one hundred (100) persons in the world,
World Population vs Memory Loss, (NOTE: Be sure to take the memory test at the end.)
Earth’s Population Statistics in Perspective. The population of Earth is around seven-point-eight (7.8) Billion. For most people, it is a large figure however, if you condensed seven-point-eight (7.8) billion into one hundred (100) persons, and then into various percentage statistics the resulting analysis is relatively much easier to comprehend.
Out of 100 :
11 are in Europe
5 are in North America
9 are in South America
15 are in Africa
60 are in Asia
49 live in the countryside
51 live in cities
75 have mobile phones
25 do not.
30 have internet access
70 do not have the availability to go online
7 received university education
93 did not attend college.
83 can read
17 are illiterate.
33 are Christians
22 are Muslims
14 are Hindus
7 are Buddhists
12 are other religions
12 have no religious beliefs.
26 live less than 14 years
66 died between 15 – 64 years of age
8 are over 65 years old.
If you have your own home, eat full meals & drink clean water, have a mobile phone, can surf the internet, and have gone to college, you are in the minuscule privileged lot. (in the less than seven percent (7%) category)
Among one hundred (100) people in the world, only eight (8) live or exceed the age of sixty-five (65).
If you are over sixty-five (65) years old, be content and very grateful. Cherish life, grasp the moment.
If you did not leave this world before the age of sixty-four (64) like the ninety-two (92) people who have gone before you, you are already the blessed amongst mankind.
Take good care of your own health. Cherish every remaining moment.
If you think you are suffering memory loss……. Anosognosia, very interesting…
In the following analysis the French Professor Bruno Dubois, Director of the Institute of Memory and Alzheimer’s Disease (IMMA) at La Pitié-Salpêtrière – Paris Hospitals, addresses the subject in a rather reassuring way:
“If anyone is aware of their memory problems, they do not have Alzheimer’s.”
1. Forget the names of families.
2. Do not remember where I put some things.
It often happens in people sixty (60) years and older that they complain that they lack memory. “The information is always in the brain, it is the “processor” that is lacking.”
This is “Anosognosia” or temporary forgetfulness.
Half of people sixty (60) and older have some symptoms that are due to age rather than disease. The most common cases are:
– forgetting the name of a person,
– going to a room in the house and not remembering why we were going there,
– a blank memory for a movie title or actor, an actress,
– a waste of time searching where we left our glasses or keys ..
After sixty (60) years of age, most people have such a difficulty, which indicates that it is not a disease but rather a characteristic due to the passage of years. Many people are concerned about these oversights hence the importance of the following statements:
1.”Those who are conscious of being forgetful have no serious problem of memory.”
2. “Those who suffer from a memory illness or Alzheimer’s, are not aware of what is happening.”
Professor Bruno Dubois, Director of IMMA, reassures the majority of people concerned about their oversights:
“The more we complain about memory loss, the less likely we are to suffer from memory sickness.”
Now for a little neurological test:
Only use your eyes!
1- Find the C in the table below!
OOOOOOOOOOOOOOOOOOOOOOOOOOOOOOO
OOOOOOOOOOOOOOOOOOOOOOOOOOOOOOO
OOOOOOOOOOOOOOOOOOOOOOOOOOOOOOO
OOOOOOOOOOOOOOOOOOOOOOOOOOOOOOO
OOOOOOOOOOOOOOOOOOOOOOOOOOOOOOO
OOOOOOOOOOOOOOOOOOOOOOOOOOOOOOO
OOOOOOOOOOOOOOOOOOOCOOOOOOOOOOO
OOOOOOOOOOOOOOOOOOOOOOOOOOOOOOO
OOOOOOOOOOOOOOOOOOOOOOOOOOOOOOO
OOOOOOOOOOOOOOOOOOOOOOOOOOOOOOO
OOOOOOOOOOOOOOOOOOOOOOOOOOOOOOO
2- If you found the C, then find the 6 in the table below.
99999999999999999999999999999999999999999999999
99999999999999999999999999999999999999999999999
99999999999999999999999999999999999999999999999
69999999999999999999999999999999999999999999999
99999999999999999999999999999999999999999999999
99999999999999999999999999999999999999999999999
3- Now find the N in the table below. Attention, it’s a little more difficult!
MMMMMMMMMMMMMMMMMMMMMMMMMMMMNMM
MMMMMMMMMMMMMMMMMMMMMMMMMMMMMMM
MMMMMMMMMMMMMMMMMMMMMMMMMMMMMMM
MMMMMMMMMMMMMMMMMMMMMMMMMMMMMMM
MMMMMMMMMMMMMMMMMMMMMMMMMMMMMMM
If you pass these three tests without problem:
– you can cancel your annual visit to the neurologist.
– your brain is in perfect shape!
– you are far from having any relationship with Alzheimer’s.
CONCLUSIONS: I AM SO RELIEVED!!!!!
Share this: