DIGITAL THEFT & BIOMETRICS
April 5, 2015
Since 1986 I have done business with a small regional bank; checking account, savings account, etc. I chose that bank, as opposed to larger national banks, due to their size, efficiency and very friendly customer relations. Good choice on my part and I have been proved correct. Let me now relate to you a conversation I had two years ago with a lady named Wanda in bookkeeping.
WANDA—Mr. Jackson have you been to Detroit lately?
JACKSON—Its’ been a very long time but no, not within four or five years.
WANDA—Well, your debit card has. There are sixteen (16) charges on your business account over the past two days. All from charges in the Detroit area.
JACKSON—What on earth are the charges?
WANDA—McDonalds twice, a pet store, two hotel bookings, a beauty salon, restaurants and there’s more.
JACKSON—None of those charges are mine and I have no idea as to how they were made.
WANDA—Have you lost your card? Did you leave it someplace?
With this question being asked, I pulled out my wallet and took a look. The card was right there.
JACKSON—Wanda, I have it right here. How could this have happened with me not having the card stolen or my losing it?
WANDA—We fight these battles every day, Bob. Here’s what we need to do; let’s close the account right now so no more charges will be made. You need to get to the bank ASAP and sign sixteen documents stating you have not made the charges shown. Can you come in today? We can reimburse your account after establishing another. Since you have fraud protection you will not lose any money but it will take about two weeks.
I left immediately for a visit to my bank and did just as she said—sign sixteen (16) individual documents stating the charges made to the establishments were fraudulent. It took the better part of an hour. I did receive reimbursement for the fraud; $ 612.58 to be exact. Let’s now take a look at the problem to see just how prevalent it is.
THE PROBLEM:
AND IT IS HUGE !!!
My card was stolen, I think, by an employee working in a Subway Sandwich Shop. He or she just lifted the necessary information from the card. As you can see from the JPEG above, one in ten Amercian consumers has been a victim of identity theft. Over one and one-half million households have had their bank accounts compromised, and these are 2009 numbers.
The amount of money stolen from me was approximately $600.00 which means I’m small potatoes to the $4,841 dollar average theft. In our country right now, that’s approximately three month’s worth of full-time work. Adding insult to injury; the out-of-pocket expense to right the situation is between $851 and $1,378.
Our credit reporting agencies do a horrible job with individual accounts which leads to seventy percent of individuals experiencing fraud having real difficulties in removing the negative numbers from their accounts.
As you can see, it takes an average time of 330 hours to repair the damage, done and to fully correct the damage requires 5,840 hours. If time is money—that’s money.
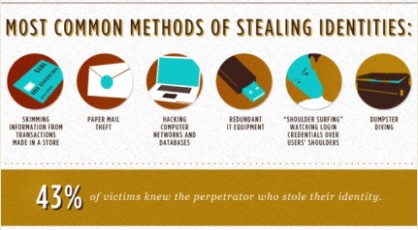
The following JPEGs will show the most common methods of stealing identities and how to protect yourself from the occurence.
BIOMETRICS:
One method to greatly lessen identity theft is the use of Biometrics. Biometrics is defined by the FBI as follows:
“Biometrics is the science and technology of measuring and analyzing biological data. It is used to uniquely identify individuals by their physical characteristics or personal behavior traits. It is used to allow employees access to certain areas and for general ID purposes. A biometrics system goes through three basic steps: 1. Acquiring data, 2. Encryption. 3. Analysis of data.
Biometrics refers to metrics related to human characteristics. Biometrics authentication (or realistic authentication) is used in computer science as a form of identification and access control. It is also used to identify individuals in groups that are under surveillance.
Biometric identifiers are the distinctive, measurable characteristics used to label and describe individuals. Biometric identifiers are often categorized as physiological versus behavioral characteristics. Physiological characteristics are related to the shape of the body. There are several types of biometric identification schemes:
- Face: the analysis of facial characteristics
- DNA
- Fingerprint: the analysis of an individual’s unique fingerprints
- Hand geometry: the analysis of the shape of the hand and the length of the fingers
- Retina: the analysis of the capillary vessels located at the back of the eye
- Iris: the analysis of the colored ring that surrounds the eye’s pupil
- Signature: the analysis of the way a person signs his name.
- Vein: the analysis of pattern of veins in the back of the hand and the wrist
- Voice: the analysis of the tone, pitch, cadence and frequency of a person’s voice.
Behavioral characteristics are related to the pattern of behavior of a person, including but not limited to rhythm, gait, and voice. Some researchers have coined the term behavior metrics to describe the latter class of biometrics.
The magnetic strip used on all American credit and debit cards is antiquated technology that has served its’ purpose. As we have seen, it certainly is and can be compromised. The charts above indicate personal experience that drives this home. A magnetic strip card is a type of card capable of storing data by modifying the magnetism of tiny iron-based magnetic particles on a band of magnetic material on the card. The magnetic strip, sometimes called swipe card or magstripe, is read by swiping past a magnetic reading head. Magnetic stripe cards are commonly used in credit cards, identity cards, and transportation tickets.
Magnetic recording on steel tape and wire was invented during World War II for recording audio. In the 1950s, magnetic recording of digital computer data on plastic tape coated with iron oxide was invented. In 1960 IBM used the magnetic tape idea to develop a reliable way of securing magnetic strips to plastic cards, under a contract with the US government for a security system. A number of International Organization for Standardization standards, ISO/IEC 7810, ISO/IEC 7811, ISO/IEC 7812, ISO/IEC 7813, ISO 8583, and ISO/IEC 4909, now define the physical properties of the card, including size, flexibility, location of the magstrip, magnetic characteristics, and data formats. They also provide the standards for financial cards, including the allocation of card number ranges to different card issuing institutions.
What if, there was a biometric access point on each credit and debit card we owned? Every time you made a purchase with a card, you had to use biometrics to complete the transaction. The metric was a singular part of the card with equipment owned and operated by the vendor or merchant to receive the biometric data supplied by each individual. What if, we do away with passwords and PINs and replace those with biometric information relative to the individual user. Specific physiological information unique to the user and more importantly the owner of the equipment itself. Cards, credit and debit, PCs, smart phones, i-pads, tablets, etc—what if. In my opinion purchase power and digital equipment are headed in this direction. We know that financial establishments in the European Union are embedding “chips” into credit cards for lessen fraud. Biometrics is much safer and will provide greater security in the long run. I think we are headed in that direction.
As always, I welcome your comments.








August 27, 2015 at 09:46
Hello! This is my first visit to your blog! We are a group of volunteers and starting a new project in a community in the same niche.
Your blog provided us useful information to work on. You have done a
outstanding job!
LikeLike
September 21, 2015 at 18:02
Hello Lingerie, Thank you so much for the very kind comments. I really appreciate you taking a look and certainly hope you will come back. Take care.
LikeLike
August 24, 2015 at 17:45
Hi, i feel that i noticed you visited my site thus i got here to go back the favor?.I am trying to find issues
to enhance my web site!I assume its adequate too use
a few of your ideas!!
LikeLike
September 24, 2016 at 11:27
Hello Innerwear. Please feel free to use any subjects write about to your benefit. Thank you so much for the very kind comments. I certainly hope you enjoyed my post and please come again. Take care.
LikeLike
August 22, 2015 at 09:10
You could definitely see your enthusiasm in the article you write.
The world hopes for even more passionate writers like you who
aren’t afraid to mention how they believe. All the
time follow your heart.
LikeLike
January 18, 2017 at 19:15
Hello Innerwear. This one was a real eye-opener when I started doing the research prior to writing. Digital Theft is a HUGE problem that is being addressed by Biometrics. Thank you so much for your very kind comment and I certainly do hope you come for other visits. Take care. Bob
LikeLike